1. How could we not list GenAI first?
Security seemed like an afterthought in the advent of GenAI foundation models, and now, GenAI presents a new threat vector. GenAI models have been found to lack security around data particularly as it is shared with other users. It has been shown that poisoning just a small amount (<1%) of the training data can compromise the models. On the other hand, GenAI is expected to dramatically increase protection against attackers. While it will have a more moderated impact on threat detection (at least in the near term), customers are increasingly looking to GenAI to reduce threat volume and are seeking solutions that prioritize and contextualize alerts. We see this manifesting with growing interest in SOARs like Swimlane, which has released a GenAI tool for Slack called Swimmy, enabling users to interact directly with their Swimlane Turbine SecOps platform via prompts in Slack.
2. Attackers will increasingly target the SMB and MM
GenAI will make it easier for attackers to find ways to leverage and exploit vulnerabilities, enable more targeted attacks, and increase their ROI, and therefore SMB and MM companies that were formerly ‘too small’ to target will increasingly be the focus of attackers. As a result, we see increased urgency among SMB and MM companies to up-level their cybersecurity stack and posture. Unlike the enterprise with dedicated cybersecurity teams managing layered best-of-breed security products, we expect thinly staffed SMB / MM customers to look for out-of-the-box, all-in-one solutions while still not compromising on efficacy. Filling this gap, we have seen SMB / MM leaders like Coro emerge with a platform designed to serve the end-to-end needs of customers with an offering built on the core tenants of simplicity, uniformity, affordability and quality. Starting at $8.99 / user / month SMB and MM companies can adopt a security solution that protects the essential core pillars of security across anti-virus, email, endpoint, cloud, SASE, MDR and more.
3. Selling cybersecurity is easier, but not easy
More decision makers are included in the sales process, with the CFO more and more involved as the final decision maker. In addition, customers are questioning if new and existing spend is required or whether products can be consolidated among vendors. Still, we are seeing certain companies accelerate their growth even in this environment. Island has viewed the CFO inclusion in the sales process as a tailwind by leveraging messaging around high ROI and augmentation of vendors to get all decision makers onboard. By replacing, consolidating, or augmenting spend across legacy VPN, DLP, CASB and other tools, Island has helped its customers drive immediate cost savings while also improving IT and security simplicity and efficacy, helping gain buy-in from CISOs, CIOs and CFOs.
4. Everything is turning into “posture management”
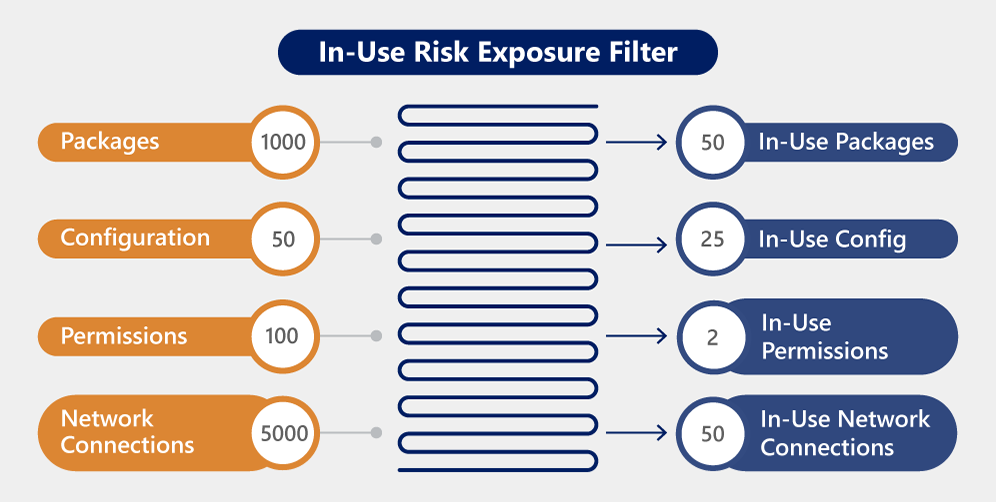
Cloud security posture management (CSPM) was the start, and now we have data security posture management (DSPM), SaaS security posture management (SSPM), application security posture management (ASPM), and even cybersecurity posture management – this is the land for future platforms and will be a buzzword going forward. Over time CSPM has become just one piece in a comprehensive Cloud-Native Application Protection Platform (CNAPP) strategy as companies look for a solution that covers all aspects of cloud security across CSPM, CWPP, CDR and CIEM. While posture management will be an important part of any security stack, the drawback is that it predominantly focuses on pre-runtime configuration without knowledge of what is pushed to production, publicly facing, or exploitable. For this reason, we see the best approach to posture management as one paired and integrated with the context and knowledge from runtime security. CNAPP leader Sysdig has leveraged its strong positioning in runtime (CWPP) plus investment in GenAI to help provide SOC analysts greater context and prioritization of alerts around vulnerabilities and threats to prevent, detect, and respond quickly to cloud attacks. By uniting the data it sees at runtime, Sysdig identifies which vulnerabilities are exploitable (see below) and critical to address, providing SOC analysts with a prioritized set of alerts to address.